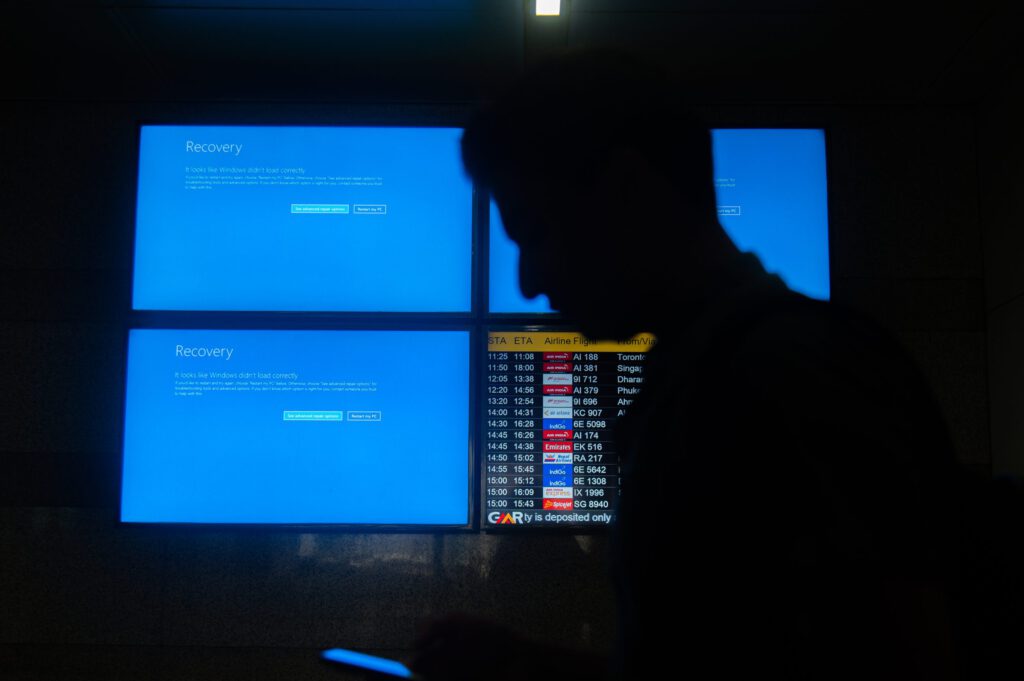
Last week’s meltdown is a belated reminder of our broader vulnerability to cyber attacks.
Vulnerabilities are dangers. That was the lesson of last week’s computer meltdown, caused by an inadvertent update to CrowdStrike’s widely used Falcon Sentinel cybersecurity software. The update crashed millions of Windows computers, wreaking havoc on air transportation, financial services and healthcare, with enormous economic and human costs.
But it could have been much worse. Few users realize that allowing automatic updates effectively exposes their computers and other devices to remote control. In another, more nefarious context, the mass takeover of computers would be called a botnet. Botnets are at the heart of the cybercrime industry. In May, the U.S. Department of Justice and the FBI arrested YunHe Wang, a Chinese national who illegally and clandestinely seized control of millions of computers around the world that run Windows software. He then rented those computers out to cybercriminals, making nearly $100 million, according to the Justice Department.
Organized crime should be considered a national security threat. It undermines public confidence in the integrity of state administration. The Kremlin is increasingly outsourcing assassinations and sabotage to gangs.
But it would be even worse if China, Russia, and Iran could turn legitimate software updates into de facto botnets, exploiting our trust in legitimate software companies to allow their spies and saboteurs to steal our data, encrypt it, and make it inaccessible across computers and networks around the world.
Western policymakers and opinion formers are so worried about the phantom threat of Russian nuclear weapons that we pay too little attention to the far more immediate national security threat to the vulnerable but deeply interconnected computer systems that underpin our economy, public services, and society.
Stay up to date
Sign up to receive regular emails and keep up to date on CEPA activities.
For example, few people noticed the most frightening near-miss in Internet history, which came to light earlier this year. Its target was far less known than CrowdStrike or Microsoft: the xy compression utility. Created and maintained by volunteers, these open-source tools are the workhorses of the software world. Anyone can inspect them and suggest improvements. If you can gain the trust of other experts, your suggestions will be implemented and become building blocks for countless other programs.
Surprisingly little is known about the perpetrator of this attack, who first emerged in November 2021 under the username JiaT75 making professional contributions to other open source projects. No one has ever met this person in person or verified his identity, but he gradually took over the task of updating xy, and eventually was able to issue an update that rendered any computer that had it installed effectively operational – effectively the master key for hundreds of millions of machines.
By chance, a conscientious Microsoft engineer named Andres Freund noticed that the trial version of xy was using slightly more memory than it should have, and was able to diagnose the flaw just before it was released to the public. Few people outside the cybersecurity industry noticed this.
The sophistication and persistence of the attack suggests that Russia’s foreign intelligence service, the SVR, is likely responsible, but the clues left behind could also be a clever double bluff to divert attention from the real culprits: China, Iran, or North Korea.
The attackers’ near success, and the difficulty in attributing it, stems from the same simple fact: the Internet was not designed with security in mind. We have no easy way to verify the identity of those we interact with, and we trust most of the information that reaches our computers.
This laid-back attitude has spurred incredible innovation and driven many costs down to near zero, but it also comes with huge hidden costs: not only do we need to update our software, but our online security culture, too.
Edward Lucas is a non-resident senior research fellow and senior advisor at the Centre for European Policy Analysis (CEPA).
Europe’s Edge is CEPA’s online journal covering key topics in European and North American foreign policy. All opinions are those of the authors and do not necessarily represent the position or views of the institutions they represent or of the Centre for European Policy Analysis.
Edge of Europe
CEPA’s online journal covers important topics related to European and North American foreign policy.
read more
Source link